Master Privileged Access Management with Ultimate Insider Evaluation Guide
Unlock the full potential of your organization's security strategy with our Ultimate Insider Evaluation Guide to Master Privileged Access Management, and discover how you can protect sensitive data, streamline operations, and enhance your cybersecurity posture—browse options and explore solutions designed to meet your unique needs today.
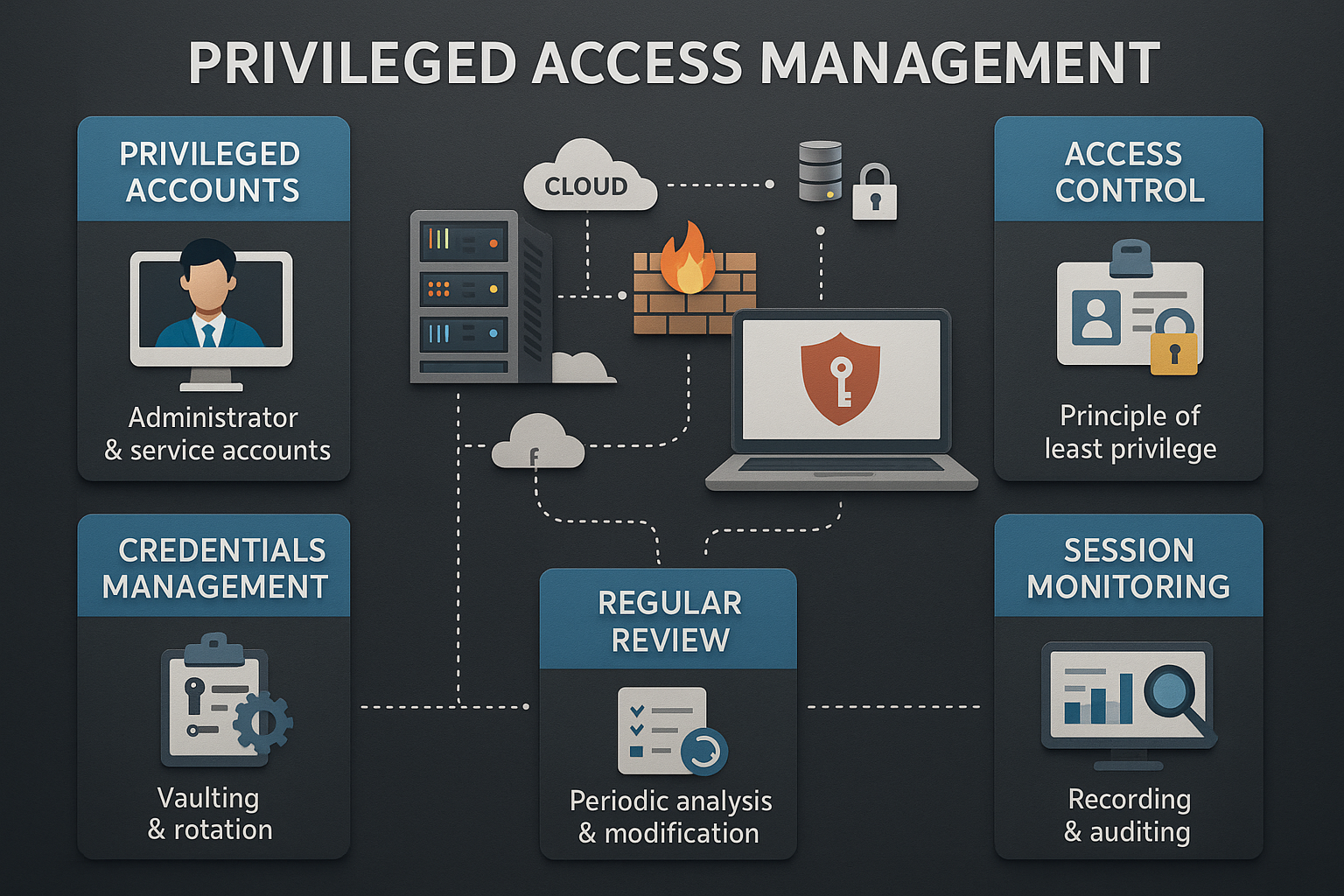
Understanding Privileged Access Management (PAM)
Privileged Access Management (PAM) is a critical component of cybersecurity that focuses on controlling and monitoring access to an organization's most sensitive information and systems. As cyber threats become increasingly sophisticated, managing privileged accounts is essential to prevent unauthorized access and data breaches. PAM solutions help organizations enforce the principle of least privilege, ensuring that users have only the access necessary to perform their jobs, thereby minimizing potential security risks.
The Importance of PAM in Today's Cybersecurity Landscape
In the current digital era, organizations are facing a growing number of cyber threats that target privileged accounts. These accounts, which have access to critical systems and data, are often the primary targets for attackers. According to a report by Gartner, 80% of data breaches involve the use of privileged credentials1. By implementing robust PAM solutions, organizations can significantly reduce the risk of unauthorized access and potential data breaches.
Key Components of an Effective PAM Strategy
An effective PAM strategy involves several key components that work together to secure privileged accounts:
- Credential Management: This involves securely storing and managing credentials for privileged accounts, often through the use of password vaults and automated password rotation.
- Session Management: Monitoring and recording privileged sessions to ensure accountability and detect suspicious activities.
- Access Control: Implementing policies that enforce the principle of least privilege and ensure that users have only the access necessary for their roles.
- Audit and Reporting: Regularly auditing privileged access activities and generating reports to maintain compliance with industry regulations.
Financial Considerations and Cost Benefits
Investing in PAM solutions can be a cost-effective strategy for organizations looking to enhance their cybersecurity posture. While the initial investment may seem significant, the potential savings from preventing data breaches and ensuring compliance with regulations can far outweigh the costs. According to a study by IBM Security, the average cost of a data breach in 2021 was $4.24 million2. By implementing PAM, organizations can mitigate these risks and avoid the financial repercussions of a breach.
Exploring PAM Solutions
There are numerous PAM solutions available on the market, each offering unique features and capabilities. Some popular options include CyberArk, BeyondTrust, and Thycotic, which provide comprehensive PAM tools tailored to different organizational needs. When exploring these options, it's important to consider factors such as scalability, ease of integration, and the ability to support hybrid and multi-cloud environments.
Real-World Examples of PAM Success
Many organizations have successfully implemented PAM solutions to enhance their security posture. For example, a global financial services company deployed a PAM solution to manage access to its critical infrastructure, resulting in a 50% reduction in security incidents3. Similarly, a healthcare provider used PAM to comply with industry regulations and protect patient data, achieving a 30% improvement in audit compliance4.
Mastering Privileged Access Management is essential for organizations looking to protect their most sensitive data and systems. By implementing a robust PAM strategy, you can reduce the risk of cyber threats, ensure compliance with industry regulations, and ultimately safeguard your organization's valuable assets. As you explore these options, remember that specialized solutions are available to meet your specific needs, and visiting websites of leading providers can offer further insights into the best PAM strategies for your organization.