Master Privileged Access Management with Ultimate Insider Evaluation Guide
Unlock the full potential of your organization's security strategy with our Ultimate Insider Evaluation Guide to Master Privileged Access Management, and discover how you can protect sensitive data, streamline operations, and enhance your cybersecurity posture—browse options and explore solutions designed to meet your unique needs today.
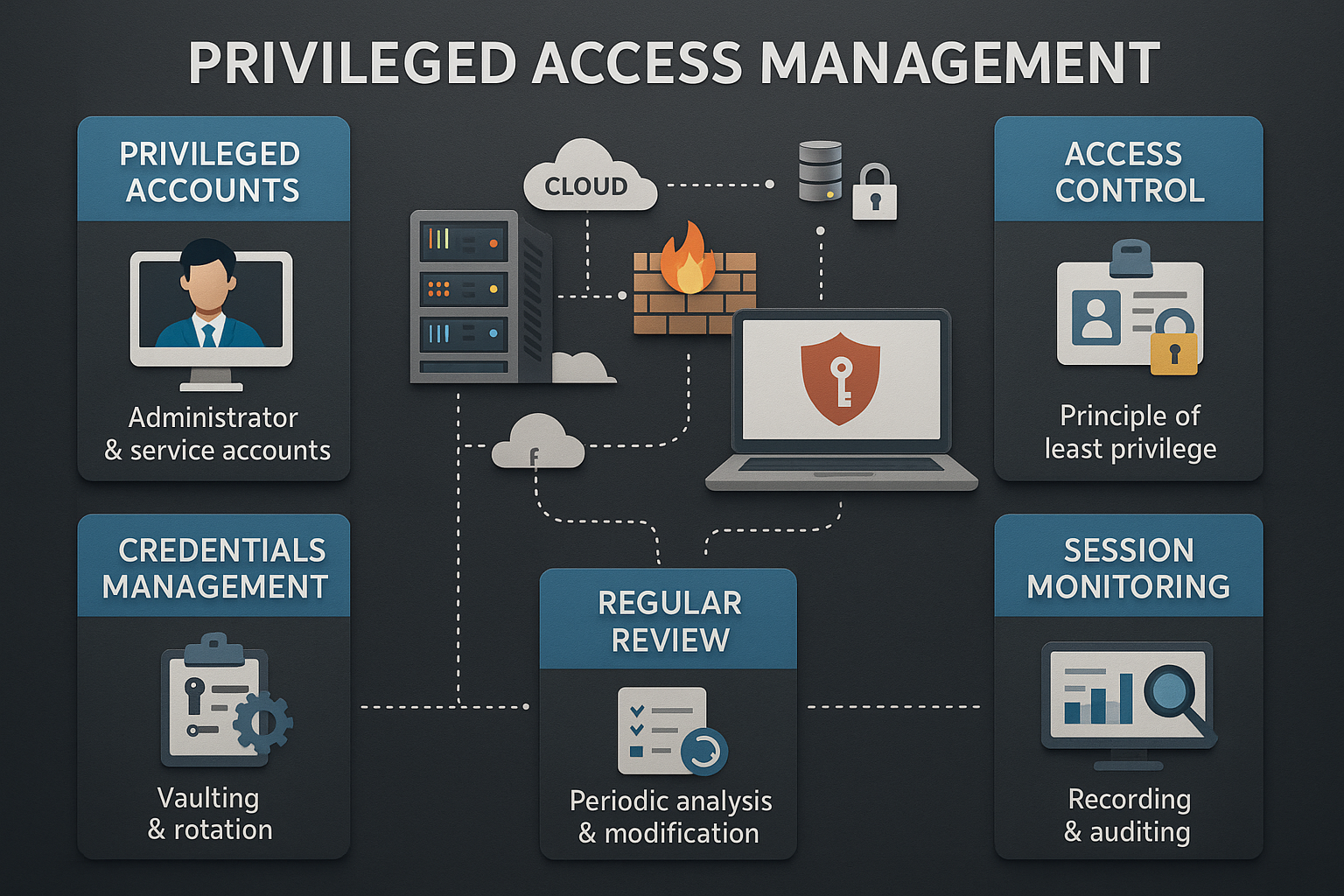
Understanding Privileged Access Management (PAM)
Privileged Access Management (PAM) is a critical component of cybersecurity that focuses on controlling and monitoring access to an organization's most sensitive information and systems. As cyber threats become increasingly sophisticated, managing privileged accounts is essential to prevent unauthorized access and data breaches. PAM solutions help organizations enforce the principle of least privilege, ensuring that users have only the access necessary to perform their jobs, thereby minimizing potential security risks.
The Importance of PAM in Today's Cybersecurity Landscape
In the current digital era, organizations are facing a growing number of cyber threats that target privileged accounts. These accounts, which have access to critical systems and data, are often the primary targets for attackers. According to a report by Gartner, 80% of data breaches involve the use of privileged credentials1. By implementing robust PAM solutions, organizations can significantly reduce the risk of unauthorized access and potential data breaches.